Speaker UNPrep
Location: Talks Lobby
Introducion
This is 3 challenges:
- open the door
- turn on the lights
- turn on the vending machine
The introduction is:
Help us get into the Speaker Unpreparedness Room!
The door is controlled by ./door, but it needs a password! If you can figure
out the password, it'll open the door right up!
Oh, and if you have extra time, maybe you can turn on the lights with ./lights
activate the vending machines with ./vending-machines? Those are a little
trickier, they have configuration files, but it'd help us a lot!
(You can do one now and come back to do the others later if you want)
We copied edit-able versions of everything into the ./lab/ folder, in case you
want to try EDITING or REMOVING the configuration files to see how the binaries
react.
Note: These don't require low-level reverse engineering, so you can put away IDA
and Ghidra (unless you WANT to use them!)
Hints
Open the door
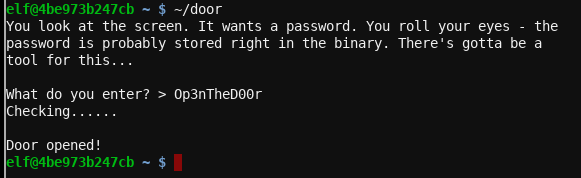
In the ~/lab run ./door and the output is:
You look at the screen. It wants a password. You roll your eyes - the
password is probably stored right in the binary. There's gotta be a
tool for this...
What do you enter? >
This suggests that running strings on the executable will be sufficient and as the password is not likely to be less than 8 characters the option -8 can used to only show strings that are longer than 8 characters.
elf@4be973b247cb ~/lab $ strings -8 door | less
Scrolling through the output, the following is found:
Be sure to finish the challenge in prod: And don't forget, the password is "Op3nTheD00r"
Trying it for real and the door is opened with Op3nTheD00r.
Answer
Op3nTheD00r
Turn on the lights
In the ~/lab run ./lights and the output is:
The speaker unpreparedness room sure is dark, you're thinking (assuming
you've opened the door; otherwise, you wonder how dark it actually is)
You wonder how to turn the lights on? If only you had some kind of hin---
>>> CONFIGURATION FILE LOADED, SELECT FIELDS DECRYPTED: /home/elf/lab/lights.conf
---t to help figure out the password... I guess you'll just have to make do!
The terminal just blinks: Welcome back, elf-technician
What do you enter? >
The contents of lights.conf:
password: E$ed633d885dcb9b2f3f0118361de4d57752712c27c5316a95d9e5e5b124
name: elf-technician
The hint indicates that perhaps the program can decrypt the password for you.
Bushy Evergreen
Hey, you want to help me figure out the light switch too? Those come in handy sometimes.
The password we need is in the lights.conf file, but it seems to be encrypted.
There's another instance of the program and configuration in ~/lab/ you can play around with.
What if we set the user name to an encrypted value?
Swap the keys in lights.conf
elf@0aea948f3432 ~/lab $ cat lights.conf
password: E$ed633d885dcb9b2f3f0118361de4d57752712c27c5316a95d9e5e5b124
name: elf-technician
elf@0aea948f3432 ~/lab $ vi lights.conf
elf@0aea948f3432 ~/lab $ cat lights.conf
name: E$ed633d885dcb9b2f3f0118361de4d57752712c27c5316a95d9e5e5b124
password: elf-technician
elf@0aea948f3432 ~/lab $ ./lights
The speaker unpreparedness room sure is dark, you're thinking (assuming
you've opened the door; otherwise, you wonder how dark it actually is)
You wonder how to turn the lights on? If only you had some kind of hin---
>>> CONFIGURATION FILE LOADED, SELECT FIELDS DECRYPTED: /home/elf/lab/lights.conf
---t to help figure out the password... I guess you'll just have to make do!
The terminal just blinks: Welcome back, Computer-TurnLightsOn
Note that on the last line the output is Computer-TurnLightsOn and not elf-technician.
The program has decrypted the password. Note the "E$" is the key to whether a decryption is attempted or not.
elf@0aea948f3432 ~ $ ~/lights
The speaker unpreparedness room sure is dark, you're thinking (assuming
you've opened the door; otherwise, you wonder how dark it actually is)
You wonder how to turn the lights on? If only you had some kind of hin---
>>> CONFIGURATION FILE LOADED, SELECT FIELDS DECRYPTED: /home/elf/lights.conf
---t to help figure out the password... I guess you'll just have to make do!
The terminal just blinks: Welcome back, elf-technician
What do you enter? > Computer-TurnLightsOn
Checking......
Lights on!
Answer
Computer-TurnLightsOn
Turn on the vending machine
In the ~/lab run ./vending-machine and the output is:
elf@973e9a9de6fb ~/lab $ ./vending-machines
The elves are hungry!
If the door's still closed or the lights are still off, you know because
you can hear them complaining about the turned-off vending machines!
You can probably make some friends if you can get them back on...
Loading configuration from: /home/elf/lab/vending-machines.json
I wonder what would happen if it couldn't find its config file? Maybe that's
something you could figure out in the lab...
Welcome, elf-maintenance! It looks like you want to turn the vending machines back on?
Please enter the vending-machine-back-on code > a
Checking......
Beep boop invalid password
If the configuration file is removed then the program prompts for a name and password.
elf@973e9a9de6fb ~/lab $ ./vending-machines
The elves are hungry!
... SNIP ...
ALERT! ALERT! Configuration file is missing! New Configuration File Creator Activated!
Please enter the name > grodo
Please enter the password > grodo
Welcome, grodo! It looks like you want to turn the vending machines back on?
Please enter the vending-machine-back-on code > grodo
Checking......
That would have enabled the vending machines!
If you have the real password, be sure to run /home/elf/vending-machines
elf@973e9a9de6fb ~/lab $ cat vending-machines.json
{
"name": "grodo",
"password": "kNfdh"
}elf@973e9a9de6fb ~/lab $
It can be seen that the pasword length matches the length of the password that is provided, but this is not a simple transposition cipher as the 'o' in 'grodo' gets changed to 2 different values, 'f' and 'h'.
The solution that was used was a bruteforce attack on the password assuming that it was an alphanumeric password.
word=''
pass=''
# these are the letters of the existing password
for l in L V E d Q P p B w r
do
word="${word}${l}"
found=0
# try each alphanumeric character in turn
for i in \
a b c d e f g h i j k l m n o p q r s t u v w x y z \
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z \
0 1 2 3 4 5 6 7 8 9
do
# delete the config file for each attempt
rm vending-machines.json
# pass input to vending-machines using a heredoc
# send output of vending-machines to /dev/null to reduce "noise"
./vending-machines <<EOF >/dev/null;
$pass$i
$pass$i
EOF
# see if there is a match with the password that is now
# in vending-machines.json
res=$(grep '"password": "'${word} vending-machines.json)
if [ -n "${res}" ]; then
# got a match so update pass
pass="$pass$i"
found=1
# move onto the next letter in the password
break
fi
done
# catch if character is not alphanumeric
if [[ $found == 0 ]]; then
echo "No match found for $l ($word)"
break
fi
echo "Password so far is: $pass"
done
echo "Password is: $pass"
This yields a password of CandyCane1
Answer
CandyCane1